I did not have a clue about what is meant by GPG when I heard it.
As it turned out to be it has to do with security.
Our team strives to have good security practices. I am no developer but I am contributing to our open-source project where any contribution needs to be signed and verified in GitHub and I had to get my head over how GPG works to understand it.
The decision to implement GPG is to prevent impersonation attacks, and be able to make sure that we only received signed and validated contributions to our repositories by our actual contributors.
Here I try to give you a high-level explanation of what it is, why it is useful and the first steps to generate your pair and start using it.
GPG in Brief
GPG serves to make your online digital life more secure.
GnuPG is also known as GPG is an open-source implementation of the PGP (Pretty Good Privacy) standard. It is essentially an asymmetric key standard that works with an interconnected set of keys.

One private, and secret and the other public, public meaning that it can be shared without any danger of misuse. Fact is, one usually uploads the public key to official online key servers, where everyone can check for someone’s public PGP or GPG keys. Here is an example, the keys.openpgp.org server.
If you were to compare with the physical world, the key servers act as phone directories where people upload their keys linked to specific email addresses.
Symmetric vs Asymmetric Keys
A Symmetric Key is a Private Key. There is no “Public” part to the Symmetric Key. If you encrypt a ZIP archive, the “password” is the Private Symmetric Key.
As Symmetric Keys allow for very fast and efficient they are used extensively within core parts of all cryptographic systems that use encryption. Here the key could be different or identical between two parties. This key is to be transmitted (or mutually derived by Diffie–Hellman) so that data can be securely transferred.
However, other than crypto developers, or when you have a shared password to a ZIP archive, no humans directly use Symmetric Keys, instead they use Asymmetric Keys.
An Asymmetric Key is a special key that has both a private and public parts. The allow for people and systems to do many convenient operations that would be impossible with only Symmetric Keys.
GPG uses Symmetric Keys internally, however in common case the uses are always directly interacting with their Asymmetric Keys.
Public and Private Keys
A Public Key allow for people share a special manipulation of their Private Key for others to interact with. The two most main interactions are:
- For Verifying a Signature matching a Public Key.
- This signature could only be generated by the Private Key that the Public Key was derived from.
- For Encrypting Data to a Public Key.
- This data can only be decrypted by the Private Key that the Public Key was derived from.
PGP and Key Purposes
PGP (and therefore GPG) defines roles, (or purposes), as additional meta-data that is encoded into the Public Keys that are generated.
- Authenticating (Not regularly used)
- Certifying (Internal use only, the main role of the Primary Key is to Certify the validity of its related Sub-Keys and User-ID’s)
- Signing
- Encrypting
If you are wondering what the difference between Authentication and Signing like I was. The difference lies in its trust foundation.
Authentication only serves to say: “Hello, this is Me”, where Signing is proving that the material is yours and validated as such by you through a digital signature.
Why to use it?
Advantages
For authentication, certification and signing the receiving end can verify that the content is from you, having your public key. On the other hand, if the other party wants to send you something only for you, they will use your public encryption key in combination with their own private key to sign and certify the content. Such content can only be decrypted using your own private key, and by having their public key you will know that it is from them.
First advantage: If someone sends to you something encrypted, meant only for you, you will be the only one capable of decrypting it.
“All right but why now, so many keys?”
Essentially there is one primary key, which is typically used only for signing and certification, and a sub-key signed by the primary key for encryption. However, you can have one for each of the usages if you wanted.
Second advantage: Each sub-key when used is transmitted at the same time, but if compromised it can be revoked individually and a new key generated while keeping your primary key valid. It makes it easier to manage your keys and split them for the different purposes you want to use them.
Disadvantage
If your primary key is compromised or you lose it, your security has been breached and someone can impersonate you or you lose access to your digital “id” stemming from this key…. you may have to start building your digital reputation from scratch.
Nevertheless, for this situation there exists the revocation certificate which is created from the start at the same time that you create your keys for the first time or at any given time for the individual keys you want to revoke. With this certificate you would have to go to the before mentioned GPG key servers and upload it, to publicly revoke the affected key or keys.
First steps
Generating your new GPG keys with default options
First of all, you need to create yourself a new pair of GPG keys.
For this, you need to download the proper software to create and manage these. You have the command line option or the GUI implementations to use this standard.
Here is a link to the GnuGPG website where you get access to all you need. I myself am using the GPG4Win it is easy to use. Their documentation is very detailed and helpful.
Once you download and install it you get a set of programs. Each for a specific purpose, however in Kleopatra, you can easily generate in less than 5 minutes your pair of keys and register them if you want at one of the existing key servers.
On the other hand, if you prefer the command-line interface here is a very good article for the first steps by Mark Schindel “How to Use GPG”.
Nevertheless, you can also have access to a series of screenshots going over this process. We created a GPG Bootcamp repository for our contributors. Here you will find a step by step guideline to create your first set of GPG Keys using two approaches in our GPG 101.
Exporting or backing up your keys
Here are some screenshots using Kleopatra:
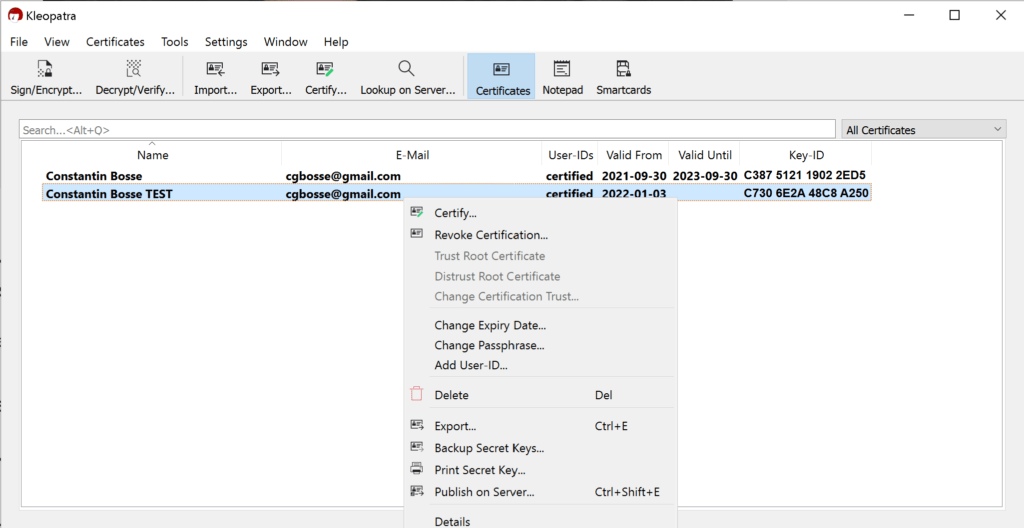
If you want to check the contents of the “.asc” file just open it with any basic text editor file.
And again a link to Mark Schindel’s “How to Use GPG” which also covers this step.
Revocation Certificate
During the process of your key creation you also generate a revocation certificate which you should download and or preferably print and back up with your keys disconnected from your online computer. To download your revocation certificate you can also follow these simple steps:
If you want to know more about it here is a link to our step by step guide GPG 101 where there is a section for regenerating your revocation certificate of a specific key.
Encrypting files
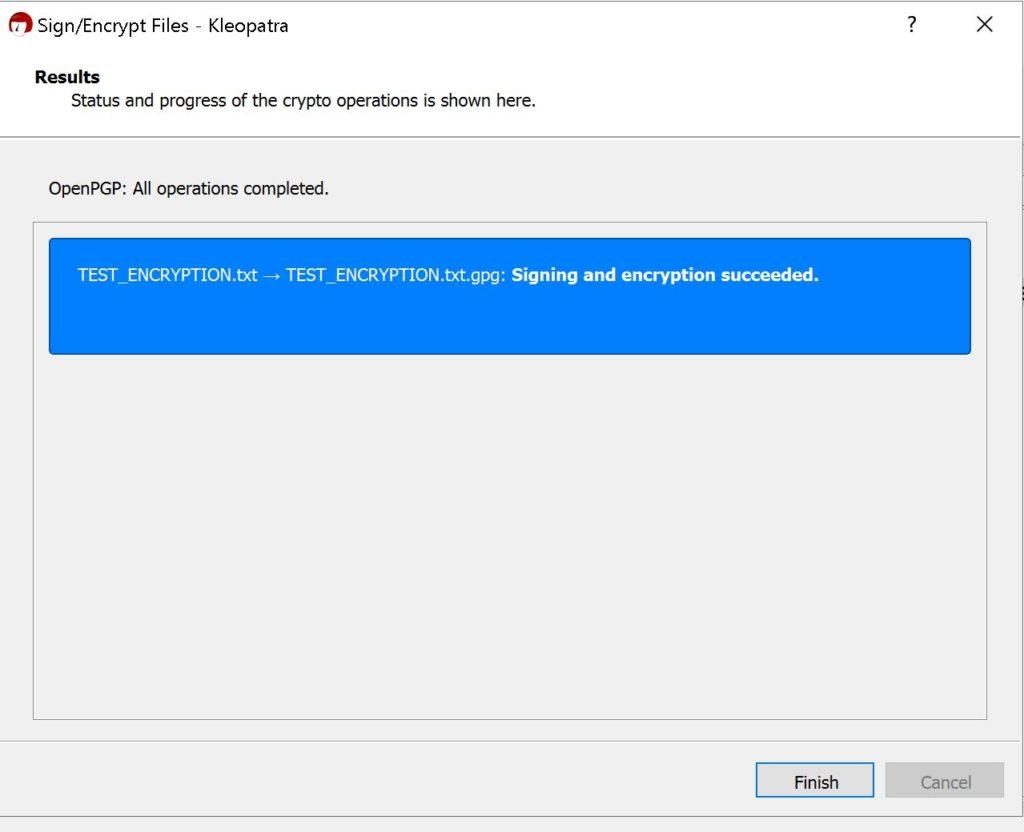
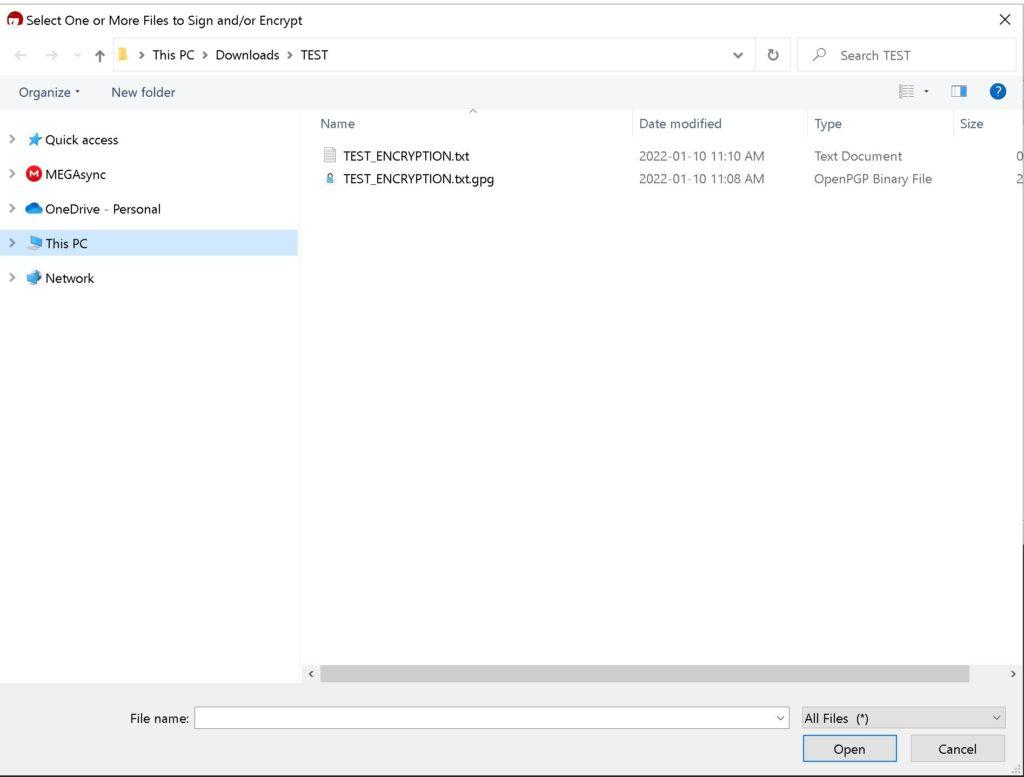
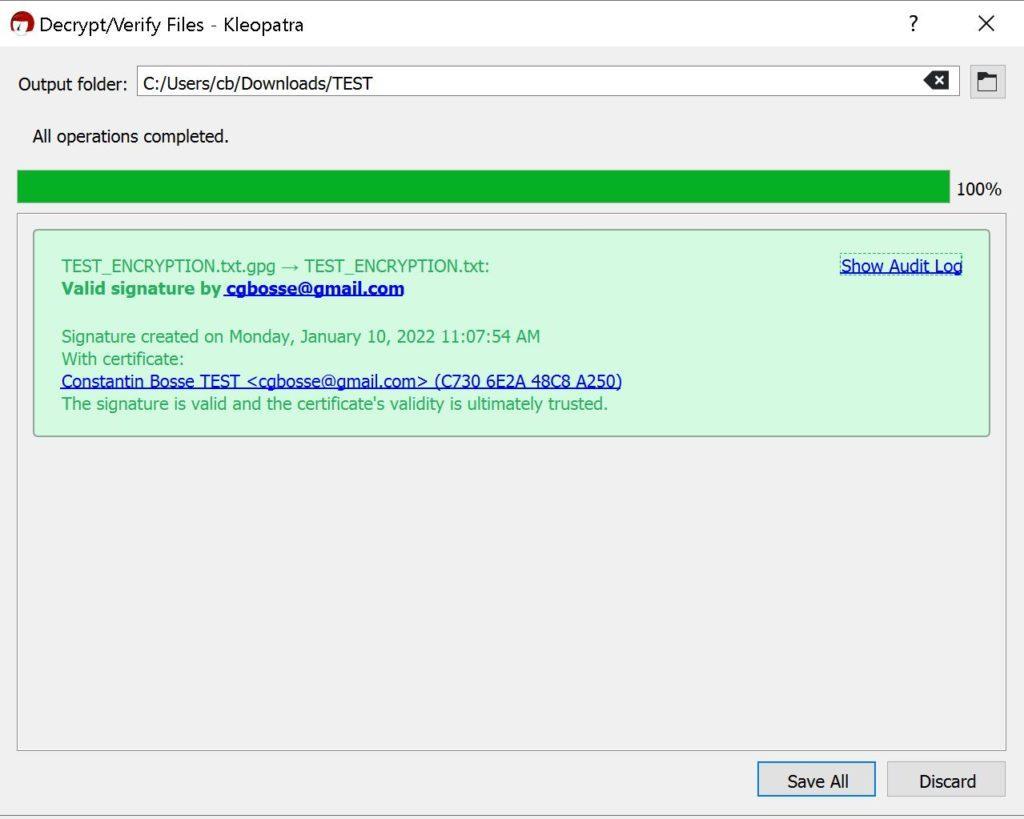
You can start using it right out of the box to encrypt files with your keys. The user interface is very intuitive.
Here are some screenshots of Kleopatra:
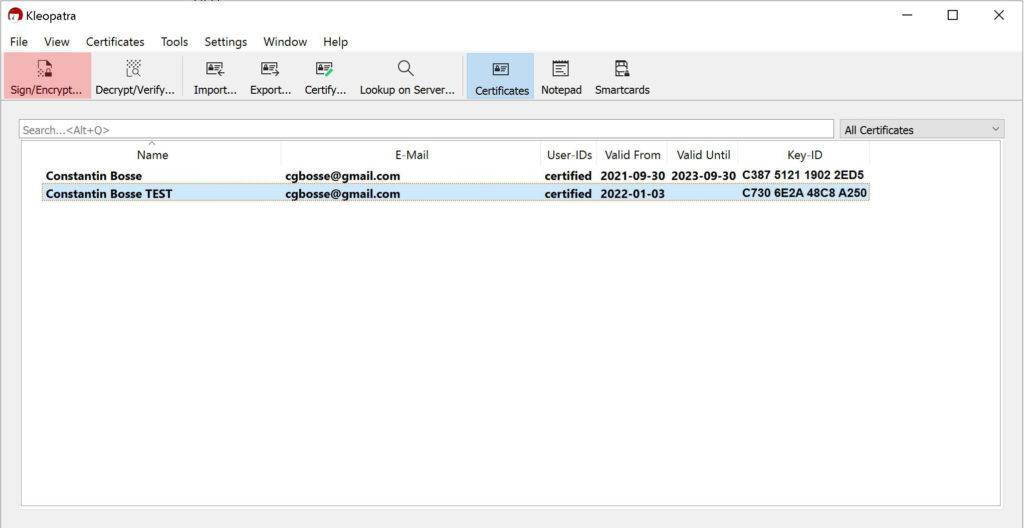
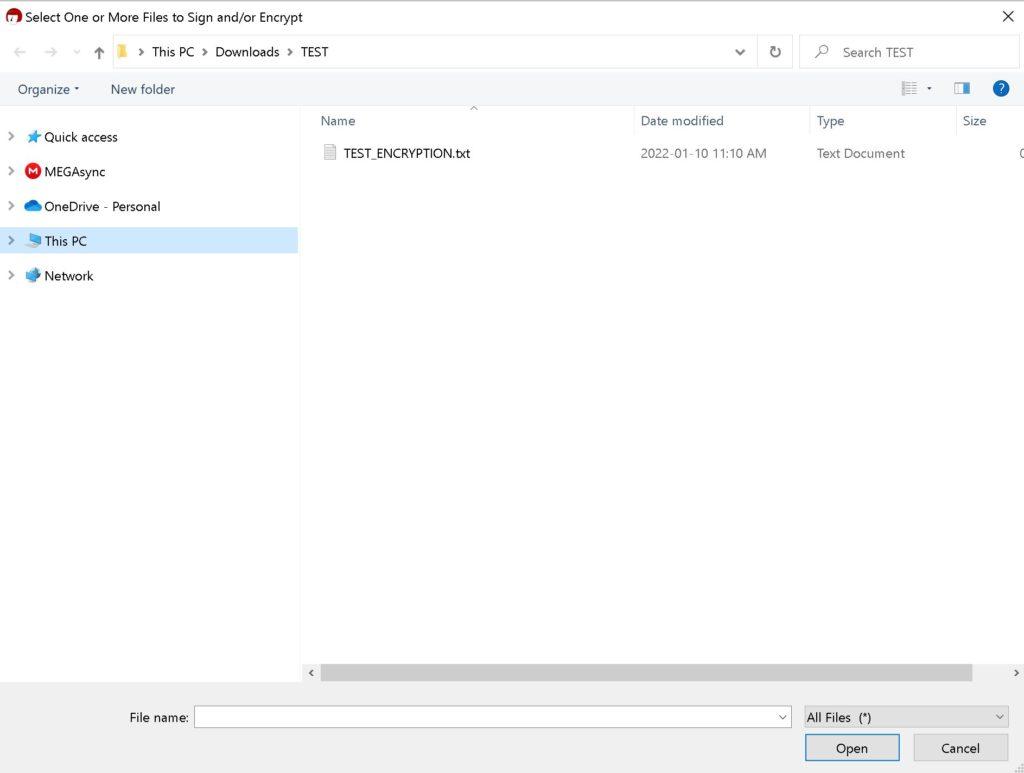
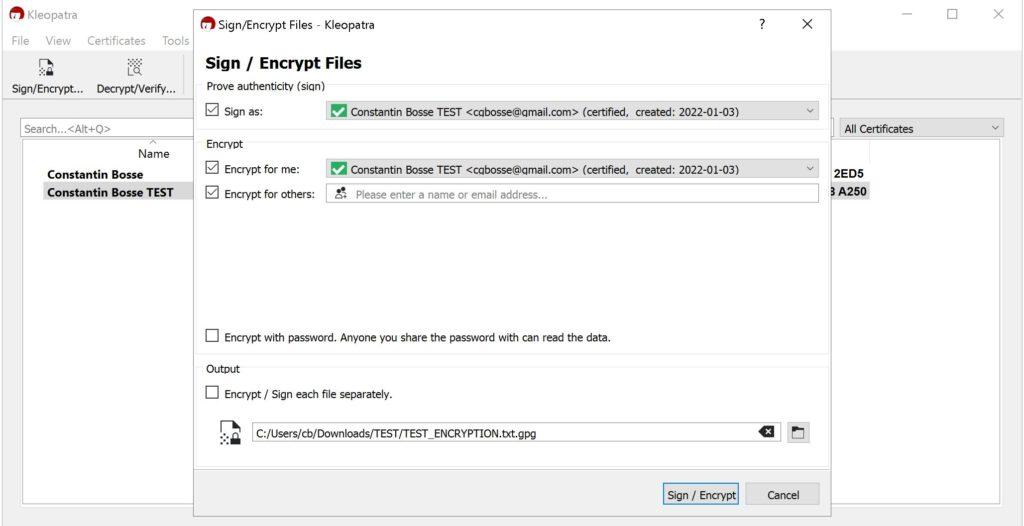
And again a link to Mark Schindel’s “How to Use GPG” which also covers this step.
As you can see it is pretty much straightforward.
Though there are some other considerations for you I will talk about in another post, some best practices to consider, as well as in another how to revoke your key.
I hope that some of your initial questions about GPG have been covered and that you are now more informed than I was when I started using it.